Proactive Cybersecurity: TIMi’s Strategic Alliance with Radically Open Security (ROS)
In an era where data and the “Clouds” are king, safeguarding your data assests is not just a necessity but the cornerstone of trust in the digital realm.
As a cloud-oriented solution, TIMi’s collaboration with Radically Open Security on a comprehensive security audit is a powerful statement of our commitment to the modern cloud technologies and to cybersecurity in general.
Why a third-party Audit? An Essential Step for Security Assurance
Understanding the need for resilience in the face of the constantly evolving Cyber threats, TIMi sought to reinforce its Cyber defenses at the position where they are at their most vulnerable: i.e. when TIMi is used to connect to a “Public Cloud”.
As a cloud-oriented solution, TIMi offers many “little boxes” (or connectors) to easily integrate with all the common “Cloud” services from the “Public Clouds”, such as Azure, Huwaei, AWS, Google, OVH, etc. But, be warned! All these connections are happening through an “untrustworthy” internet connection that is subject to any sort of Cyber Attacks. Security is key.
One “Public cloud” in particular, Azure, uses a set of non-standard connection protocols that were more complex to secure than the others.
This is why we took the decision to partner with ROS for a security audit of the Azure Cloud connections inside TIMi. This audit was driven by our determination to preemptively identify and fortify potential vulnerabilities, ensuring the safety of our clients’ data.
Marcus Bointon’s Expertise: Translating Findings into Fortifications
We selected the “Radically Open Security” (ROS) company to perform the Pentest (penetration testing) because of their exemplary track record: They did already ensure pentesting exercices for many well-known high-tech software companies such as: Google, Mozilla, the European Commission, etc. More details on this subject here. We are in good company!
Leading the charge was Marcus Bointon, a pentester renowned for his prowess in cybersecurity. Under his guidance, the audit provided us with valuable insights, leading to immediate enhancements of the security of our code. For our non-technical stakeholders, this meant not just strengthening firewalls but weaving security into the very fabric of our software.
After a few iterations and improvements on our code, ROS finally approved it: Our code is now good for a 100% secure usage! Here is an extract of the final report from ROS that demonstrates the quality and robustness of our code against Cyber Threats: “We consider the code to be sufficiently robust and free of vulnerabilities that would represent a significant threat”.
If you are interested in the whole Pentest report from Radically Open Security, you can consult it here.
Embracing Security as a Continuous Journey
The ROS report emphasized a critical tenet: Security is not a one-off checkmark but a relentless pursuit of excellence. Following their recommendations, TIMi has instituted regular security assessments and significant development process improvements to adapt proactively to the ever-changing cyber threat landscape.
Acknowledging Collaborative Success
Our journey towards heightened security was a collaborative endeavor, enriched by ROS’s expertise. Their not-for-profit ethos and dedication to ethical practices are in lockstep with our principles at TIMi, echoing our mutual goal for a safer, more ethical digital world.
In Conclusion
At TIMi, we are commited to create the best, most secure cloud-solution available today.
Our experience with ROS serves as a clear indicator of our proactive stance on cybersecurity.
We invite our clients and partners to visit our website and our Youtube channel for more details about the integration between TIMi and the public clouds.
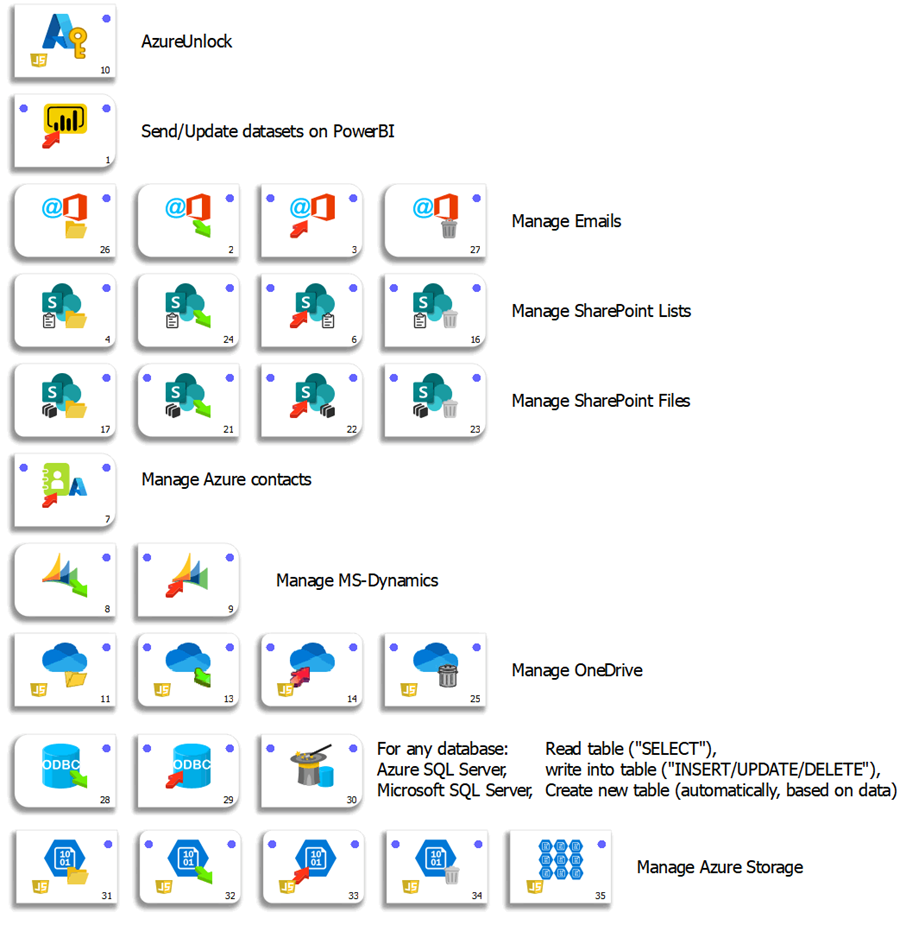
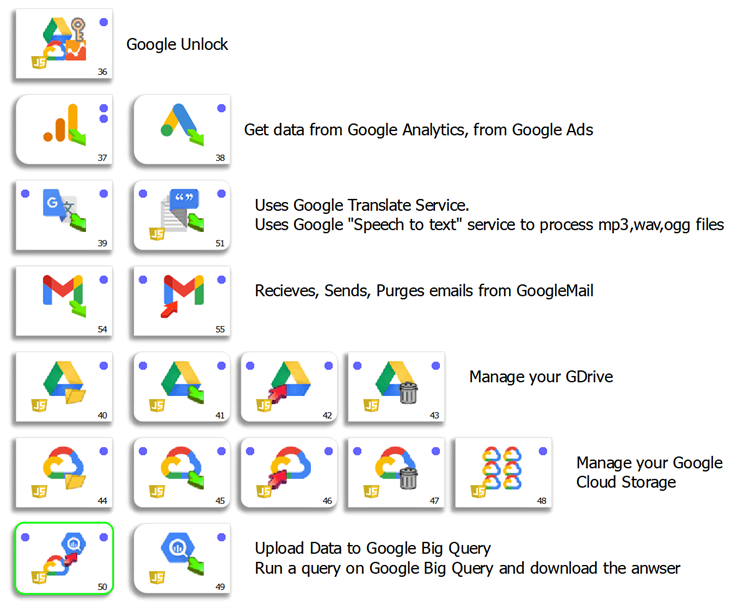
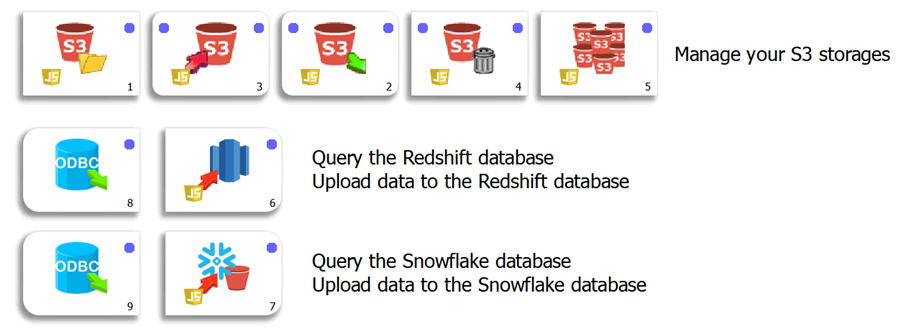
As part of our dedication to create a true hybrid solution (i.e. a solution that is both a “cloud-oriented” solution and a “on-premise” solution), we strive to provide inside TIMi the connectors to ALL the common “Clouds Services”. Here is a small screenshot of the most common connectors:
Azure Connectors
Google
AWS
Huawei
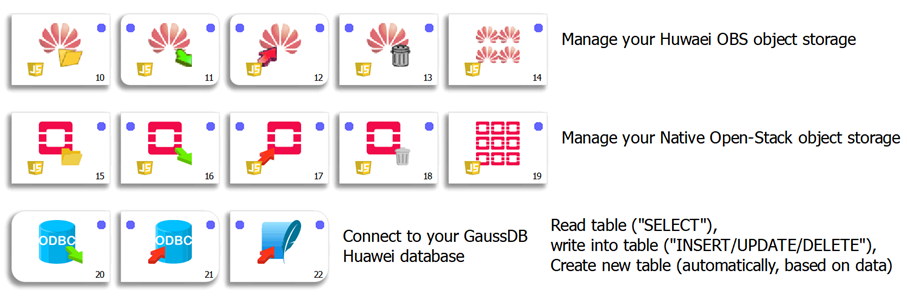
Other Common Cloud Services
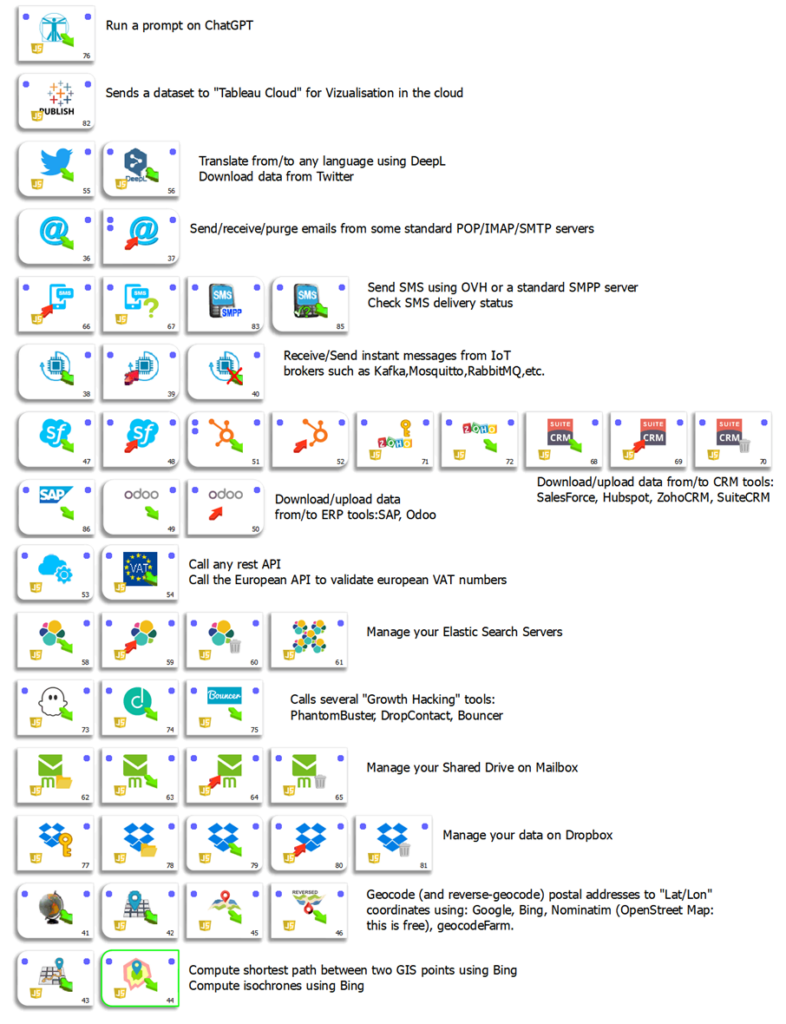
You’ll find more details about these connectors inside the one-line Anatella user-guide here.
Click here to contact us for more information about our solutions.